What is a database security audit? Compendium of knowledge.
7 October 2024
Reading time: 26 minutes

In today’s increasingly digital world, data is one of an organization’s most valuable resources. Companies, government institutions, as well as individual users collect and store huge amounts of information, which is essential for conducting business, market analysis, or providing various services. In this context, data security becomes increasingly important – any vulnerability or negligence can lead to disastrous consequences, such as data leaks, hacking attacks, loss of reputation or huge financial losses. One of the key elements in maintaining an adequate level of information protection is conducting regular database security audits.
Check our article to learn more about what a database security audit is, its components, and the benefits of performing one. This is a complete compendium of knowledge about database security audits.
The importance of data in today’s world
Data today is seen as the “gold of the XXI century.” – It is the foundation of business operations, and access to it and the ability to process it can determine competitive advantage. Organizations analyze data to make decisions, personalize services and predict consumer behavior. Over the past few years, the amount of information being processed has increased significantly, making database systems a key component of IT infrastructure. Databases store different types of information, including customer data, financial transactions, product information, health data or sensitive data.
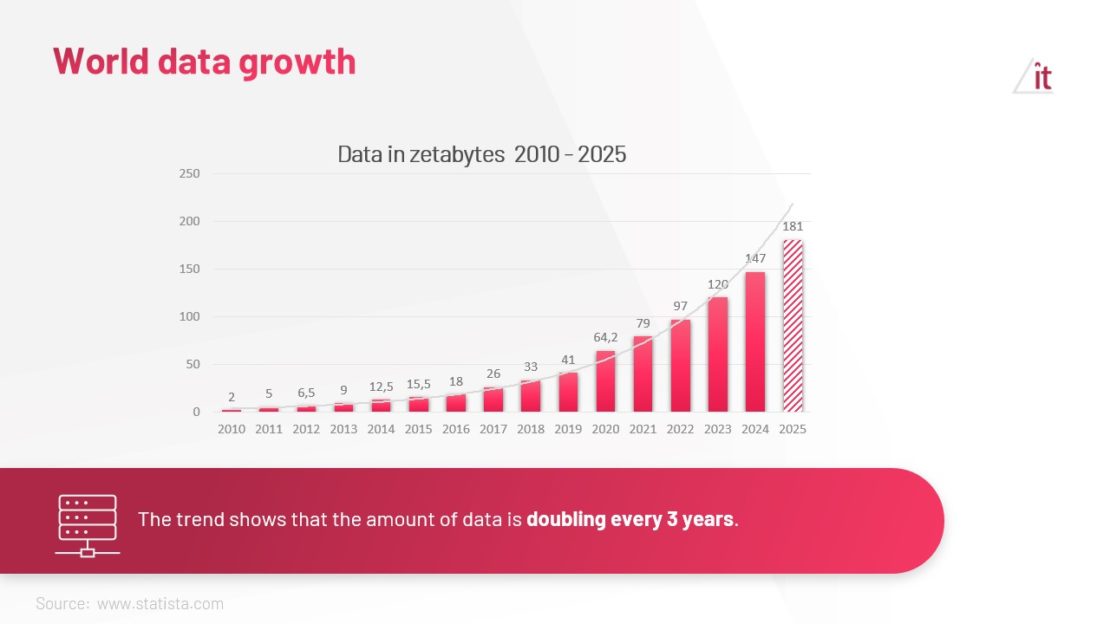
Risks associated with inadequate database protection
With the growing importance of data, the number of threats targeting databases is increasing. Cybercriminals are constantly evolving their methods in an attempt to gain unauthorized access to data in order to steal, manipulate or encrypt it (e.g. through ransomware attacks). Security lapses can lead to data leaks that not only expose companies to financial losses, but can also result in serious legal consequences, especially in the context of stringent data protection regulations such as the European Union’s RODO (GDPR).
In addition, data security breaches can lead to a loss of customer trust, which has a direct impact on a company’s reputation and long-term business relationships. Examples of such incidents in recent years show how painful the consequences of not having adequate security measures can be.

Why are IT database security audits crucial?
Database security audits are systematic processes that detect, analyze and fix security vulnerabilities. Their main purpose is to ensure that data stored in databases is protected from unauthorized access, modification, as well as from illegal destruction. Regular audits make it possible to identify vulnerabilities in database systems that can be exploited by cybercriminals on an ongoing basis.
The audit checks various aspects of security, from access control to backup policies to regulatory compliance. In this way, an organization can not only effectively secure its data, but also avoid potential financial penalties resulting from non-compliance with legal requirements, such as the aforementioned RODO.
Regular audits also help maintain high quality security processes over the long term, as technologies and attack methods are constantly evolving. New threats can emerge as technology evolves, which is why it is so important for a company to be able to adapt its security to the dynamically changing threat environment. What’s more, an audit can also serve an educational function – it indicates in which areas IT teams should improve their competence and which technologies are worth implementing to minimize the risk of future incidents.
A database security audit is not a one-time activity, but an ongoing process that should be an integral part of any data protection strategy. Regularly assessing the state of security and implementing appropriate corrective actions are key steps in ensuring protection against increasingly sophisticated cyber threats.
What is a database security audit?
A database security audit is a systematic process of assessing, analyzing and verifying security measures to protect data stored in the database. The main objective of the audit is to identify potential security gaps, inadequacies in access policies and data management procedures, and to assess whether systems meet legal and regulatory requirements, such as RODO (GDPR), HIPAA or PCI-DSS.
Definition of a security audit
A database security audit involves a detailed analysis of existing systems and practices designed to protect data. This audit covers both technical aspects, such as database configuration and the security protocols used, as well as procedural approaches, such as user access management and regularity of backups. Its task is to identify which elements of the system are potentially vulnerable to attacks, and to recommend corrective and optimization measures to minimize the risk.
Unlike penetration testing, which aims to simulate actual attacks to identify potential vulnerabilities, a security audit is a more comprehensive and systematic process. It includes not only verification of a system’s vulnerability to attacks, but also an assessment of regulatory compliance and the effectiveness of security processes and data management policies.
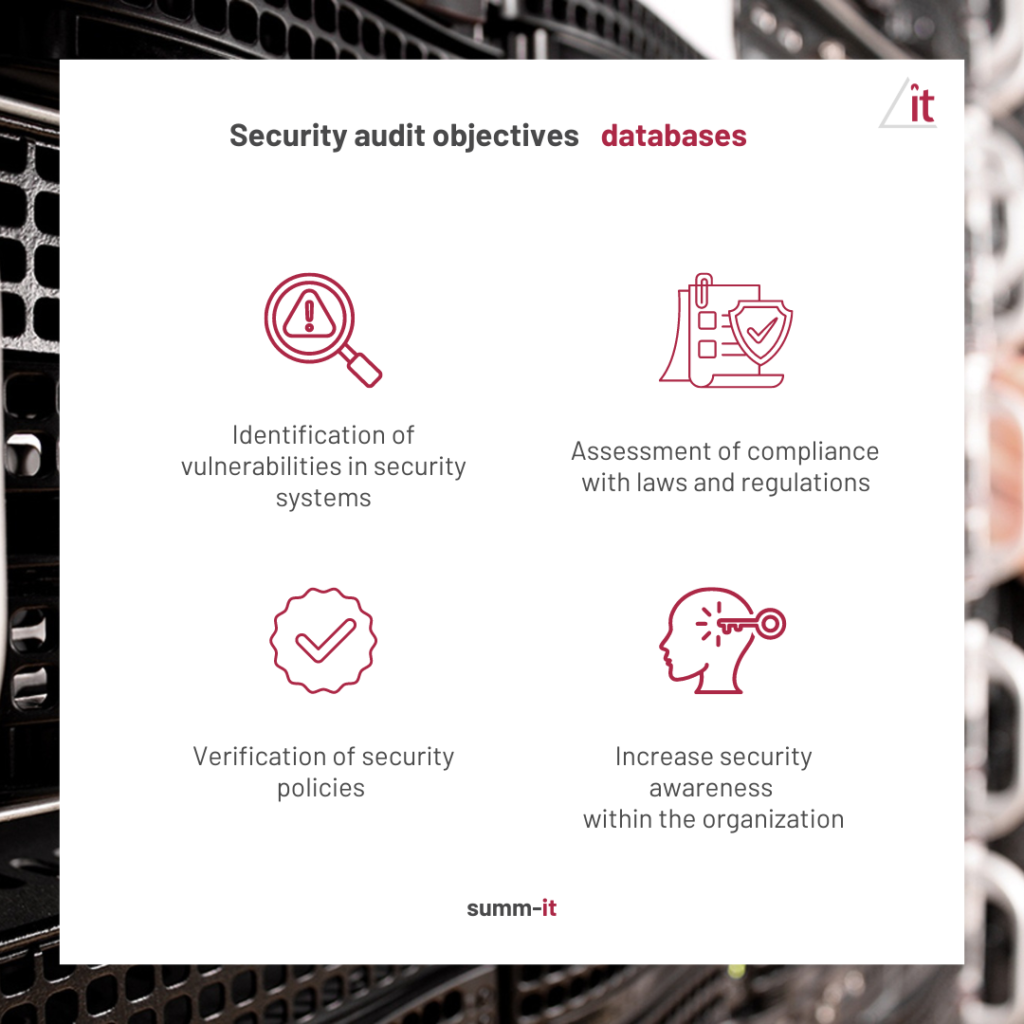
IT audit objectives on database security
The audit has several key objectives, which can be divided into several main areas:
Identification of vulnerabilities in security systems
The purpose of the audit is to find places where security systems may not be working properly. This can range from technical errors, such as misconfigured permissions or lack of data encryption, to procedural problems, such as lack of regular backups or inadequate user management policies.
Verification of security policies
Organizations often have defined security policies that specify how data is to be protected, who has access to databases and what procedures must be followed. An audit verifies that these policies are appropriate, up-to-date and that they are actually implemented in daily operations. It can also recommend changes to the policies that will improve the overall level of security.
Assessment of compliance with laws and regulations
Many industries, such as finance, healthcare and e-commerce, are subject to strict data protection regulations. Examples include RODO (GDPR) in the European Union, HIPAA in the U.S. healthcare sector, and PCI-DSS for companies processing card payments. A security audit assesses whether database systems are compliant with these regulations, and what changes are needed to meet legal requirements. Non-compliance can lead to financial penalties or other legal consequences.
Increase security awareness in the organization
An IT audit also serves an educational function. The specialists conducting it can point out to IT and database administration teams areas where changes or fixes are needed. This allows employees to better understand the risks and methods of protecting data, which is key to keeping security high in the long run.
The main elements of a database security audit
A database security audit consists of several key steps and elements that enable a comprehensive assessment of the state of security:
Evaluation of database configurations
The audit begins with an analysis of the configuration of the database itself. Elements such as user privilege settings, the way data is stored, the authentication mechanisms used, and available security features such as encryption of data in motion and at rest are checked.
Evaluation of access and identity management procedures
Another important element of the audit is to verify who has access to the database, what roles and permissions are assigned to individual users, and what procedures are in place for granting or revoking access. The audit checks for overly broad privileges assigned to users, which could lead to unauthorized access to data.
Evaluation of backup and recovery policies
The audit also includes an assessment of backup and recovery processes. It examines whether regular backups are made, how long they are kept, whether they are adequately protected against unauthorized access, and whether recovery procedures are effectively tested.
Evaluation of monitoring and event recording
A key component of database security is proper monitoring of activity. The audit verifies what monitoring mechanisms are in place, whether logs of user and system activity are recorded, and whether they are regularly analyzed for suspicious activity. In the event of a security breach, a quick response based on the logs can prevent more serious consequences.
Vulnerability and compliance testing
The audit also includes vulnerability testing, which helps identify gaps in technical security. In addition, auditors check the system’s compliance with the organization’s internal security standards and legal regulations.

Benefits of conducting an IT audit
A database security audit allows you to:
- Identify and fix security vulnerabilities before they are exploited by cybercriminals.
- Comply with applicable regulations and avoid potential financial penalties.
- Increase awareness within the organization of potential threats and security best practices.
- Increase the level of trust customers and business partners have in the organization by ensuring that data is protected to the highest standards.
In summary, a database security audit is an essential component of a comprehensive information protection strategy. Conducting regular audits minimizes the risk of attacks, allows you to meet regulatory requirements, and builds a culture of security within your organization.
Main areas of database security audit
A database security audit covers many key aspects to assess how effectively an organization is protecting its data. Each of these areas requires detailed analysis to ensure comprehensive protection against potential threats. Below is a description of the key areas on which a database security audit focuses.
Why is this important?
Database access control is one of the key elements of security. Inadequate management of user privileges can lead to unauthorized access, which in turn increases the risk of data theft, modification or even destruction.
What is being checked?
Auditors assess how user accounts are managed, what permissions individual users have, and whether mechanisms are in place to minimize access according to the principle of least privilege. Examples of detailed activities include:
- Assigning roles and privileges: The audit verifies that users only have access to the resources they need to do their jobs, and that there are no instances of excessive privileges.
- Authentication mechanisms: The ways in which users log into the database are evaluated – whether strong passwords, multi-factor authentication (MFA) are used, and whether access to the database is properly monitored.
- Time-based access management: The audit looks at whether there is a system in place for granting permissions for a specific period of time, especially for administrative access or access for external partners.
- Account lockout policies: Procedures for locking or deleting the accounts of users who no longer need access to the database, such as when a partnership ends or a position changes, are reviewed.
Examples of problems:
- Overly broad permissions for users.
- Lack of regular reviews of accounts and roles.
- Use of weak passwords or lack of MFA.
- Outdated accounts of employees who no longer work for the company.
Data security on the move and at rest
Why is this important?
Data in databases must be protected both during storage (resting) and during transfer between different systems (movement). The lack of adequate encryption mechanisms increases the risk that data will be intercepted by third parties.
What is being checked?
A database security audit analyzes whether data is adequately protected both during storage and transmission. The following aspects are checked:
- Data encryption at rest: It assesses whether the data stored in the database is encrypted, and if so, what encryption algorithm is used (e.g. AES-256).
- Encryption of data in motion: It is checked whether the data being transmitted between the database server and the client is protected by secure protocols (e.g. SSL/TLS) to prevent interception during transmission.
- Encryption key management: Auditors assess how an organization manages encryption keys – whether they are securely stored and regularly rotated.
- Integration with Data Loss Prevention (DLP) solutions: The audit assesses whether the organization uses DLP tools to help prevent data leakage, both in motion and at rest.
Examples of problems:
- Lack of data encryption at rest or use of outdated algorithms.
- Transmission of data without using secure protocols.
- Inadequate management of encryption keys.
Policies for creating and storing backups
Why is this important?
Backups (backups) are a key element in ensuring business continuity and protecting data from loss. Lack of proper backup procedures or improper storage of backups can lead to irreparable data loss.
What is being checked?
A database security audit analyzes whether backup and storage policies are properly implemented and effective. Checked are:
- Frequency of backups: Whether backups are made regularly and according to a specific schedule (e.g., daily, weekly).
- Testing of data recovery procedures: Auditors check whether the organization regularly tests the ability to restore data from backups to ensure that they are usable in the event of a disaster.
- Backup security: They assess whether backups are adequately protected from unauthorized access (e.g., encrypted and stored in a secure location separate from the main system).
- Storage of backups: Auditors check how long backups are kept and whether they are stored in different locations to minimize the risk of physical damage (e.g., fire, flooding).
Examples of problems:
- Lack of regular backups.
- Untested data recovery procedures.
- Backups stored in the same location as the main data.
Monitoring and recording of events
Why is this important?
Monitoring database activity allows early detection of unusual activity that may indicate security breaches, such as unauthorized access attempts or data manipulation.
What is being checked?
The database security audit checks what activity monitoring mechanisms are in place and how the organization analyzes and responds to suspicious events. Aspects checked include:
- Logging: Evaluates whether all relevant activities (user logins, data changes, database access attempts) are logged.
- SIEM (Security Information and Event Management) systems: Auditors check whether the organization uses SIEM systems that automatically analyze logs for suspicious activity.
- Incident Response: The audit assesses how quickly and effectively the organization responds to incidents detected in logs or monitoring – whether established procedures are in place to ensure prompt action.
Examples of problems:
- Lack of monitoring of key events.
- Insufficient analysis of logs.
- Late response to incidents.
Security against SQL Injection attacks and other threats
Why is this important?
SQL Injection attacks are among the most common threats to databases, allowing attackers to manipulate SQL queries to gain unauthorized access to data. There are also many other threats, such as DDoS attacks, which can cripple database systems.
What is being checked?
The audit analyzes how effectively databases are secured against various types of attacks. Checked are:
- SQL Injection Protection: It is evaluated whether SQL queries are adequately protected against the possibility of malicious code injection, such as by using parameterized queries.
- Use of Web Application Firewall (WAF) tools: Auditors check whether the organization uses application firewalls that can block malicious SQL queries before they reach the database.
- Penetration testing: Regularly testing systems for vulnerability helps identify potential threats.
Examples of problems:
- Lack of protection against SQL Injection.
- Inadequate penetration testing.
- Lack of real-time attack detection and blocking mechanisms.
An audit of these key areas allows for a comprehensive assessment of database security and the identification of vulnerabilities that could pose a threat to the organization.
Tools used in database security audits
A database security audit requires the use of specialized tools that help identify potential vulnerabilities, assess security features and ensure that data is protected in accordance with best practices and applicable regulations. These tools vary in functionality, but all are designed to facilitate thorough database analysis, threat detection and activity monitoring. Below is an overview of the major categories of tools and examples of their applications.
Vulnerability Scanners Tools
What are they?
Vulnerability scanning tools are applications that automatically search a database for known vulnerabilities and threats. These can include configuration errors, outdated software versions that contain vulnerabilities, and improper management of user privileges.
How do they work?
These tools analyze databases, looking for inconsistencies with security best practices. They use a database of known vulnerabilities (e.g., CVEs – Common Vulnerabilities and Exposures) and compare it to the software version and database configuration to identify potential threats.
Examples of tools:
- Nessus: A popular vulnerability scanning tool that can search database servers for software and configuration-related vulnerabilities.
- QualysGuard: A scanning tool that offers comprehensive analysis of database vulnerabilities, with the ability to track regulatory compliance.
- OpenVAS: A free open-source vulnerability scanner that can scan databases for known vulnerabilities.
Why are they used?
Vulnerability scanners quickly identify the most critical vulnerabilities that can be exploited by attackers. They are often used early in an audit to identify vulnerabilities that require immediate intervention.
Access Control & Privilege Auditing tools for managing access and privileges
What are they?
These tools help audit database security by analyzing how user accounts are managed, what permissions individual users have and what access policies are implemented. Improperly managed permissions are one of the main causes of security breaches.
How do they work?
These tools monitor which user accounts have access to specific database resources, what permissions they have (e.g., read, write, modify), and whether those permissions comply with the company’s security policy. In addition, they monitor database access in real time, identifying unauthorized login attempts.
Examples of tools:
- IBMGuardium: This is an advanced database monitoring and auditing tool that allows you to track user activities, control access and report on incidents.
- Oracle Database Vault: A privilege management tool that restricts access even for privileged users, thus improving protection against unauthorized access.
- Netwrix Auditor: Enables detailed monitoring of user activity and management of database changes, supporting compliance with regulations such as RODO and HIPAA.
Why are they used?
These tools help ensure that access to databases is properly controlled and that users have only the minimum necessary permissions.
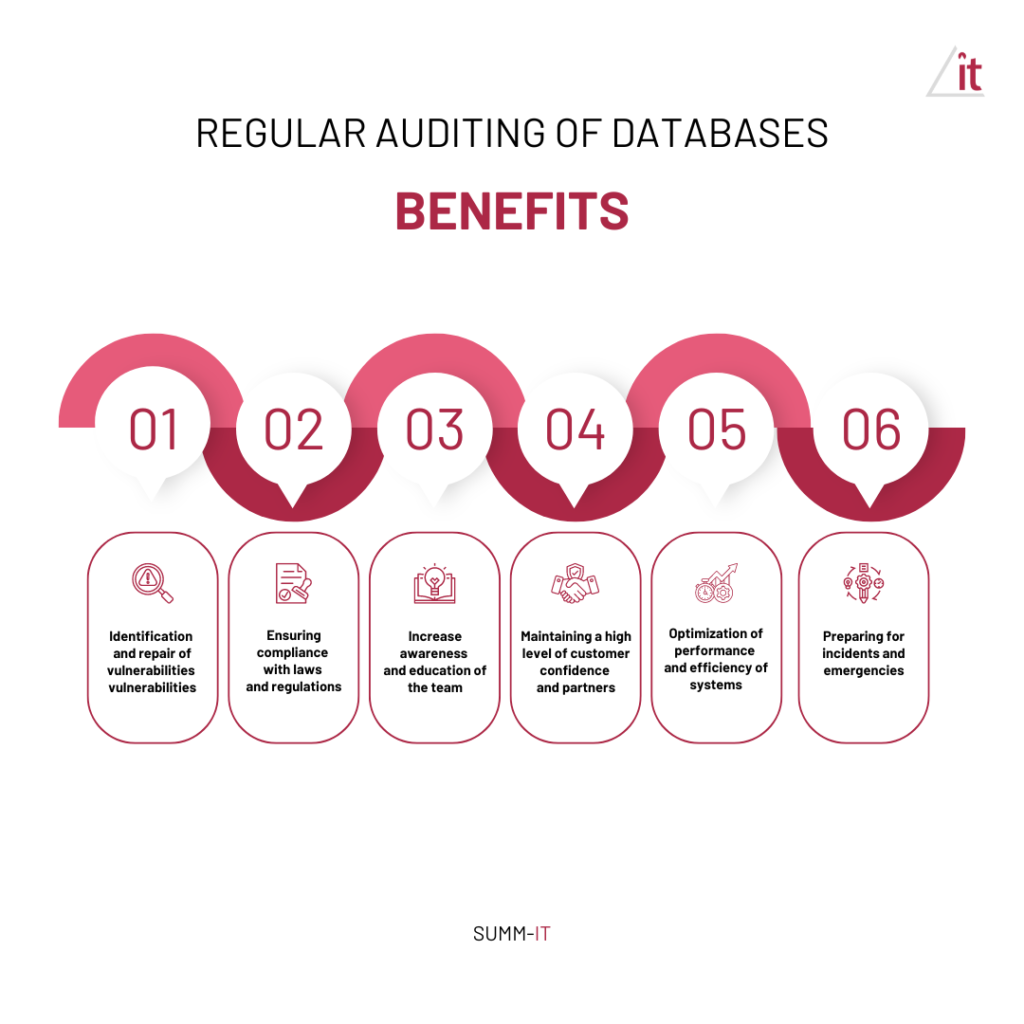
Benefits of regular database auditing
Regular auditing of databases brings many benefits to organizations, allowing them to maintain a high level of security and regulatory compliance. Below we detail the benefits of conducting database security audits.
Identification and repair of security vulnerabilities
Regular audits help identify database security vulnerabilities in real time, before they are exploited by attackers.
A database security audit allows for a detailed examination of configurations, security policies and threat protection mechanisms. This can identify areas that are particularly vulnerable to attacks, such as outdated software, misconfigured permissions or lack of data encryption. Once these vulnerabilities are identified, the organization can implement appropriate countermeasures to fix them, minimizing the risk of potential attacks.
If an audit reveals that the database is using outdated versions of software that are vulnerable to known attacks, the organization can perform updates and implement the latest security patches before these vulnerabilities are exploited by cybercriminals.
Ensure compliance with laws and regulations
A database security audit is crucial to ensure compliance with applicable laws and industry regulations, which can prevent serious financial and legal penalties.
Many laws, such as RODO (GDPR), HIPAA and PCI-DSS, impose obligations regarding data protection and information security. Regular audits help organizations ensure that their practices and procedures comply with these regulations. Auditors can assess whether security policies comply with legal requirements and identify areas for improvement.
A database security audit may reveal that an organization is not using appropriate encryption mechanisms for personal data as required by the RODO. As a result of the audit, the organization can adjust its procedures, implementing data encryption at rest and in motion, to meet regulatory requirements.
Increase awareness and education of the team
A database security audit increases security awareness within an organization and educates the IT team on best practices and risks.
During audits, security specialists often conduct training sessions or present reports that help IT teams better understand threats and how to mitigate them. Regular audits allow employees to learn about new threats, trends and best practices in database security.
If a database security audit reveals that employees are not following proper password management practices (e.g., using weak passwords), the organization can provide training on how to create strong passwords and implement password management policies.
Maintain a high level of customer and partner confidence
Regular security audits help maintain the trust of customers and business partners by ensuring that data is properly protected.
Data security is a key driver of customer and partner trust. Organizations that regularly conduct database security audits and take corrective action demonstrate their commitment to data protection. This, in turn, can improve a company’s reputation, increase customer loyalty and attract new business partners.
An organization that can document regular audits and effective corrective actions is more credible in the eyes of customers, who are more likely to entrust it with their personal or financial data.
Optimize the performance and efficiency of systems
A database security audit can also lead to optimization of system performance and efficiency, resulting in better service quality and lower operating costs.
During an audit, not only security aspects are analyzed, but also database performance and efficiency. Auditors can identify areas where performance can be improved, such as suboptimal queries, redundant data or inefficient indexing. Optimizing these items can lead to faster application performance, lower data storage costs and better overall system efficiency.
If an audit reveals that certain SQL queries are inefficient and causing the application to slow down, the organization can perform query optimization and implement better indexing, which will improve system performance and user satisfaction.
Preparing for incidents and emergencies
Regular audits help prepare for security incidents and failures by improving crisis management and recovery procedures.
A database security audit can identify weaknesses in incident management and recovery plans, allowing them to be improved. This includes checking procedures for rapid incident response, testing recovery plans, and implementing effective detection and response mechanisms. Regular audits help to continuously improve these procedures, enhancing the organization’s ability to effectively deal with potential security incidents.
If an audit reveals that the recovery plan is not regularly tested, the organization can conduct incident simulations to ensure that procedures are working properly and that the team knows how to respond in the event of an incident.
Summary
Regular auditing of databases is a key component of information security management strategies. The benefits of audits include identifying and remediating security vulnerabilities, ensuring compliance, increasing team awareness, maintaining customer trust, optimizing performance, and preparing for incidents. With these benefits, organizations can not only improve the security of their data, but also increase operational efficiency and build a stronger reputation in the market.
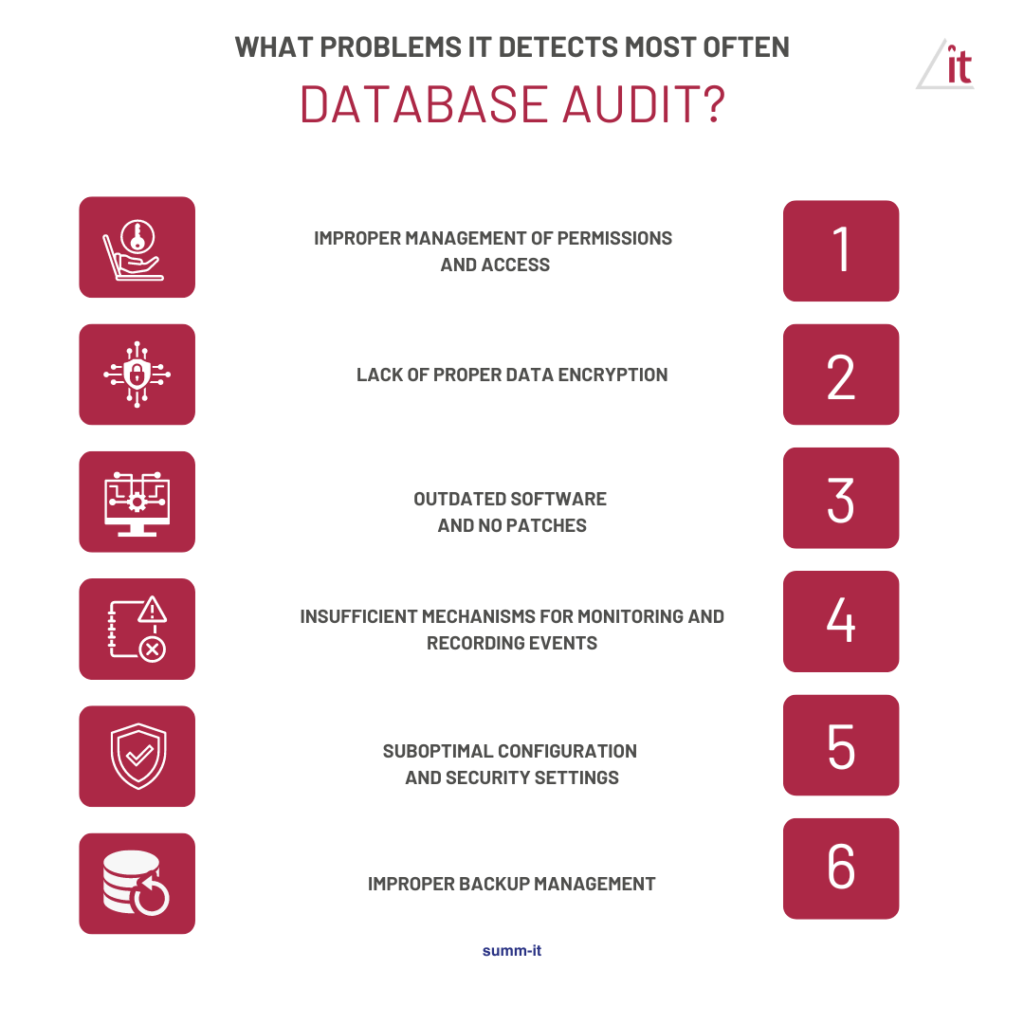
The most common problems detected during audits
During database security audits, auditors often encounter a variety of problems that can significantly affect data security and integrity. The most common problems detected during such audits and their potential consequences are described below.
Improper management of permissions and access
One of the most common problems detected during audits is improper management of user privileges and database access. This can include granting overly broad privileges, lack of regular privilege reviews, or uncontrolled role assignments.
Potential consequences:
- Uncontrolled access: Users may have access to data or functions that they do not need to perform their duties, increasing the risk of unauthorized access and data manipulation.
- Increased risk of errors and abuse: Broad permissions can lead to inadvertent errors or intentional abuse, which can expose data to deletion or modification.
A user who should only have access to reading data also has the authority to modify or delete it, which can lead to unauthorized changes in the data.
Lack of proper data encryption
Another common problem is the lack of data encryption both at rest and in motion. This can include unencrypted disk storage and a failure to protect data transferred between the server and client applications.
Potential consequences:
- Data interception and theft: If data is stored or transmitted unencrypted, it can be intercepted by attackers, leading to the theft of sensitive information.
- Invasion of privacy: Lack of encryption increases the risk of violating the privacy of users and customers, which can lead to serious legal and reputational consequences.
Customers’ personal information, such as credit card numbers, is stored unencrypted in the database, making it easy to intercept if the database is attacked.
Outdated software and no patches
Outdated software and failure to implement security patches are a common problem. Many organizations do not regularly update their database software or apply the latest patches, leaving them vulnerable to known vulnerabilities.
Potential consequences:
- Exploitation of known vulnerabilities: Attackers can use known vulnerabilities in outdated software to launch attacks such as SQL Injection and buffer overflow attacks.
- Increased risk: Outdated software increases the overall risk of security breaches and can lead to serious operational problems.
The database uses an older version of the software, which contains known security vulnerabilities that have been patched in newer versions, but have not been applied to the system.
Insufficient mechanisms for monitoring and recording events
Lack of adequate monitoring mechanisms and database event logging can lead to failure to detect security incidents and difficulties in analyzing suspicious activity.
Potential consequences:
- Failure to detect attacks: Lack of monitoring can prevent real-time detection of attacks, delaying response and increasing potential losses.
- Investigation problems: The lack of detailed logs makes it difficult to analyze incidents and investigate the causes of incidents, which can hinder security improvements.
Lack of logging of important activities, such as attempts to log into the database or changes to the table structure, making it impossible to analyze and identify potential incidents.
Suboptimal configuration and security settings
Suboptimal database configuration, including incorrect settings or lack of security, can lead to serious security vulnerabilities. This can include incorrectly configured authentication mechanisms, lack of restrictions on external access, or improper data storage settings.
Potential consequences:
- Increased risk of attacks: Improper configurations can create vulnerabilities that can be exploited by attackers to gain access to sensitive data or take control of the database.
- Data integrity issues: Suboptimal settings can lead to data integrity problems, such as unauthorized changes or data loss.
The database is configured to accept connections from any IP address, which increases the risk of access from unauthorized sources.
Improper backup management
Backup management problems, such as lack of backup encryption, lack of regular restore testing, or storing backups in unsecured locations, can lead to data loss and disaster recovery problems.
Potential consequences:
- Data loss: If backups are not properly secured or tested, they can be useless when they need to be restored, leading to the loss of important data.
- Data security: Unencrypted backups can be intercepted, leading to the leakage of sensitive information.
The backups are stored in the same location as the main database, without encryption, leaving them at risk of theft or deletion in the event of a physical attack.
Summary
During database security audits, the most common problems detected include improper privilege management, lack of data encryption, outdated software, insufficient monitoring mechanisms, sub-optimal configurations and problems with backup management. Identifying and fixing these problems are key to ensuring data security, protection against attacks and regulatory compliance. Regular database security audits help organizations maintain a high level of security and operational efficiency.
How often to perform a database security audit?
Database security is a dynamic area that requires constant attention and monitoring. The frequency of database security audits depends on many factors, including the size of the organization, the type of data, regulations and the changing threat landscape. Below I provide detailed guidelines and factors that should influence the decision on audit frequency.
Type and sensitivity of data
The type of data stored in databases is crucial in determining the frequency of audits. Sensitive personal data, financial data, or health information require special protection and therefore more frequent audits.
Recommendations:
- Sensitive data: Databases storing personal data, credit card numbers or medical information should be audited at least every 6-12 months. More frequent audits may be required if the data is particularly sensitive or if the organization operates in a high-risk industry such as finance or healthcare.
- Non-sensitive data: Databases storing less sensitive data may require audits on a less regular basis, such as once every 12-18 months.
An organization that stores and processes health data may opt for a security audit every 6 months to ensure compliance with strict regulations such as HIPAA.
Changes to the system and infrastructure
Any change to an IT system or infrastructure, including software updates, configuration changes, introduction of new applications or data migrations, can introduce new risks and security vulnerabilities.
Recommendations:
- After major changes: Audits should be conducted after any major change to the system. This could include database updates, configuration changes, introduction of new applications or migration to the cloud. Such an audit helps ensure that the changes have not introduced new security vulnerabilities.
- Before and after introducing new technologies: Any introduction of new technologies should be preceded by an audit to assess security and potential risks.
After migrating data to a new database management system, the organization conducts a database security audit to ensure that the new configuration is secure and complies with security policies.
Regulatory and industry requirements
Many industries are regulated by laws that impose requirements for the frequency of safety audits. These regulations may vary by region and industry.
Recommendations:
- Industry regulations: Organizations must comply with regulatory requirements for security audits. For example, according to PCI-DSS (Payment Card Industry Data Security Standard), audits must be conducted at least once a year.
- Local regulations: Regulations such as RODO in the European Union may require regular reviews and audits to ensure compliance with data protection regulations.
According to PCI-DSS requirements, an organization that processes payment card data must conduct a security audit at least once a year and after any major change to the system.
Trends and the changing threat landscape
With the growing number and complexity of cyber threats, organizations need to adjust audit frequency to match the changing threat landscape. New attack techniques and exploits may require more regular audits.
Recommendations:
- Threat monitoring: Organizations should track the latest threat trends and adjust audit frequency in response to new threats. If significant new threats emerge, it may be necessary to increase audit frequency.
- Incident response: If an organization experiences a security incident, it should conduct an audit to assess the causes of the incident and implement corrective actions.
After discovering a new type of ransomware attack, an organization may opt for an additional audit to verify that its systems are adequately protected against the new threat.
Size and complexity of the organization
The size and complexity of an organization can also affect the frequency of audits. Larger organizations with more complex IT structures may need more regular audits.
Recommendations:
- Large organizations: In larger organizations, where database systems are more extensive and complex, audits are recommended every 6-12 months. Regular audits help manage complexity and maintain security.
- Small and medium-sized enterprises: Smaller organizations can conduct audits every 12-18 months, depending on the specifics and risks associated with their data.
A global corporation with multiple databases spread across different locations conducts security audits every six months to manage a complex IT environment and ensure consistent data security.
The frequency of database security audits should be tailored to the type and sensitivity of data, system changes, regulatory requirements, the changing threat landscape, and the size and complexity of the organization. Regular audits help identify and remediate security vulnerabilities, ensure regulatory compliance and adaptation to changing threats. Determining the optimal frequency of audits is key to effectively managing database security and protecting against potential threats.
Summary
A database security audit is a fundamental tool in information security management that allows organizations to systematically assess and improve their security measures. Its purpose is to identify security vulnerabilities that can be exploited by cybercriminals to gain unauthorized access or manipulate data. Conducting regular audits allows these vulnerabilities to be quickly detected and remediated, which is key to preventing potential security incidents. Without regular audits, organizations can be at risk of unknowingly leaving critical vulnerabilities in the system, which can lead to serious consequences.
Adhering to audit frequency recommendations is important for maintaining a high level of database security. Audits that are too infrequent can lead to security neglect, especially in a rapidly changing IT environment. Regular audits help keep safeguards up-to-date and monitored, which is essential to adapt to new threats and regulatory requirements. Determining the optimal frequency of audits, taking into account the specifics of the organization and the type of data processed, is key to effective security management.
Identifying the most common problems during audits enables organizations to effectively manage risks. Problems such as improper privilege management, lack of data encryption or outdated software can pose serious threats to information security. Regular audits help identify these problems so that effective solutions can be implemented and security policies improved. This allows organizations to effectively prevent security incidents and ensure that their systems are adequately protected from threats.
Finally, conducting database security audits contributes to improving the overall efficiency of systems. Analyzing the results of audits allows optimization of database configurations, which can lead to improved performance and better availability. Improving the efficiency of systems not only affects better data management, but also user and customer satisfaction. Regular audits are therefore not only a tool for securing data, but also an important element in the pursuit of efficient and stable management of IT infrastructure.
What’s next?
Your data is one of your company’s most valuable assets. Are you sure they are properly protected from threats? Don’t wait until it’s too late – take care of your database security today!
With summ-it you can conduct a comprehensive database security audit, which will allow you to identify potential vulnerabilities and implement effective protection solutions. With our services, you will not only gain confidence that your data is safe, but also compliance with legal and industry regulations.
Our experienced specialists will conduct a thorough analysis, assess the current state of security and propose optimal solutions tailored to your organization’s needs. Regular audits will help you avoid costly security incidents and ensure the smooth operation of your system.
Don’t risk the security of your data – contact us now and schedule an audit! Together we will make sure that your databases are always one step ahead of threats. Trust the professionals and focus on what you do best – we’ll take care of the rest.



