Modern companies operate in an environment where data is one of the most valuable resources.
The increase in cyberattacks, increasingly sophisticated hacking methods, and growing regulatory requirements mean that IT security policy is not only a matter of good practice, but a necessity.
In this article, we explain what IT security policy is, why it is worth implementing, and how to do so effectively, step by step.
What is IT security policy?
An IT security policy is a formal document that defines the rules, procedures, and standards for protecting a company’s IT resources. It covers both technical and organizational aspects, and its main purpose is to minimize the risk associated with security incidents.
In practice, IT security policy regulates, among other things:
- who has access to data and on what terms,
- how systems and networks are protected,
- how to respond to security incidents,
- what are the responsibilities of employees in terms of cybersecurity.
Such a document should be regularly updated and adapted to changing threats and legal requirements.
Why is an IT security policy essential?
The lack of a consistent security policy can lead to serious consequences:
- Loss of data – both customer and internal data.
- Operational downtime – resulting from hacker attacks or system failures.
- Financial penalties – for non-compliance with regulations, e.g., RODO or NIS 2.
- Loss of reputation – which can result in the loss of customers and business partners.
Implementing an IT security policy is not only an obligation, but also a way to build competitive advantage. Companies that care about data security are perceived as more reliable and professional.
Key elements of IT security policy
A well-designed IT security policy should include:

- Access management
- User roles and permissions.
- Rules for granting and revoking access.
- Multi-factor authentication (MFA).
- Data security
- Encryption of data at rest and in transit.
- Regular backups and recovery tests.
- Data retention policy.
- Incident management
- Reporting and escalation procedures.
- Computer Security Incident Response Team (CSIRT).
- Incident documentation and analysis.
- Physical and environmental security
- Server room access control.
- Monitoring and physical security.
- Employee training and awareness
- Regular educational campaigns.
- Phishing simulations.
- Cyber hygiene knowledge tests.
- Regulatory compliance
- GDPR, ISO 27001, NIS 2.
- Internal compliance audits.
How to implement an IT security policy?

Step 1: IT security audit
The first step is to assess the current state of security. At summ-it, we offer comprehensive IT audits that allow us to identify gaps, assess risks, and prepare recommendations tailored to the specific needs of your company.
Step 2: Policy development
Based on the audit results, security policy documentation is created. It should be:
- compliant with applicable regulations,
- tailored to the organizational structure,
- understandable to all employees.
Step 3: Team training
Even the best procedures will not work without people’s commitment. Therefore, it is crucial to:
- train employees on the policy rules,
- build awareness of threats,
- implement a security culture.
Step 4: Implementation and monitoring
Once the document has been approved, you should:
- implement the policy in your daily work,
- monitor compliance with the rules,
- regularly update the documentation.
The most common mistakes in implementing security policies
- Lack of management involvement – IT security is not just the responsibility of the IT department, but of the entire organization.
- Overly general documentation – policies must be specific and tailored to the realities of the company.
- Lack of training – employees are often the weakest link.
- Lack of testing and auditing – policies must be verified in practice.
How does summ-it support companies in the field of IT security?
As an IT company with experience in projects for various sectors, we offer:
- NIS 2 compliance audit and GDPR database compliance audit,
- development and implementation of security policies,
- employee training,
- incident monitoring and strategic consulting.
Learn more: NIS 2 compliance audit – summ-it
Checklist: Does your company have an effective IT security policy?
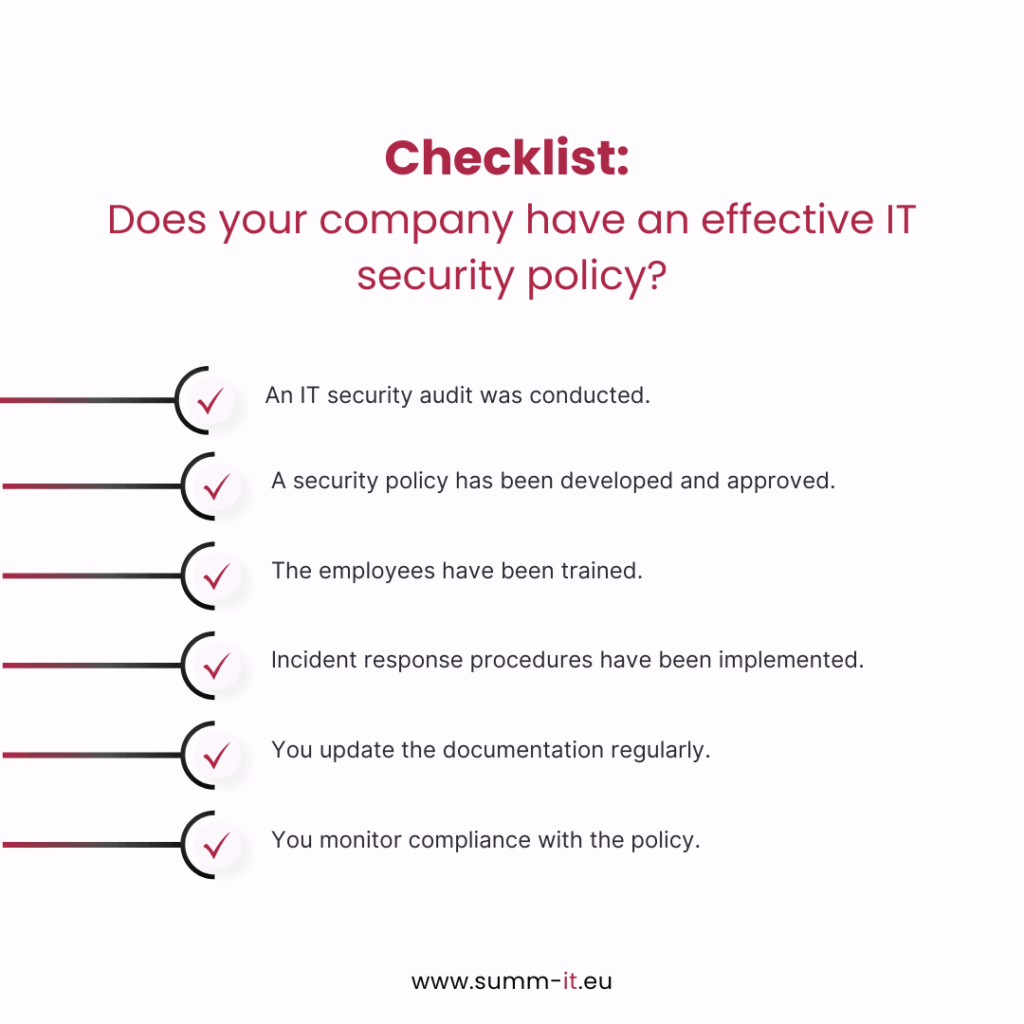
- An IT security audit has been conducted.
- A security policy has been developed and approved.
- Employees have been trained.
- Incident response procedures have been implemented.
- You regularly update documentation.
- You monitor compliance with the policy.
FAQ – Frequently asked questions
Does every company need to have an IT security policy?
Yes, regardless of size. Even small businesses process personal data and are vulnerable to cyberattacks.
Is an IT security policy legally mandatory?
In many cases, yes—for example, for companies covered by the NIS 2 Directive, GDPR, or ISO 27001. Failure to have a policy in place may result in penalties.
How often should the policy be updated?
It is recommended to review at least once a year or after each security incident.
Summary
In a rapidly changing digital environment, IT security policy is a key element of responsible organizational management. It is not only a set of technical procedures, but above all an expression of a conscious approach to protecting information resources, ensuring business continuity, and building trust in business relationships.
Its implementation allows you to organize processes, define roles and responsibilities, and effectively respond to threats that can have a real impact on the operational stability and reputation of your company. A properly developed IT security policy is not a one-time project – it is an element of organizational culture that should evolve with the development of technology, regulations, and business needs.
Modern enterprises, regardless of their scale of operation, should treat information security as an integral part of their development strategy – not only in the context of regulatory compliance, but above all as the foundation of sustainable and responsible business practices.